Xssy is a new (at least for me) platform, developed and maintained by https://github.com/paj28 and packed with free content from the growing community they are building.
The Platform
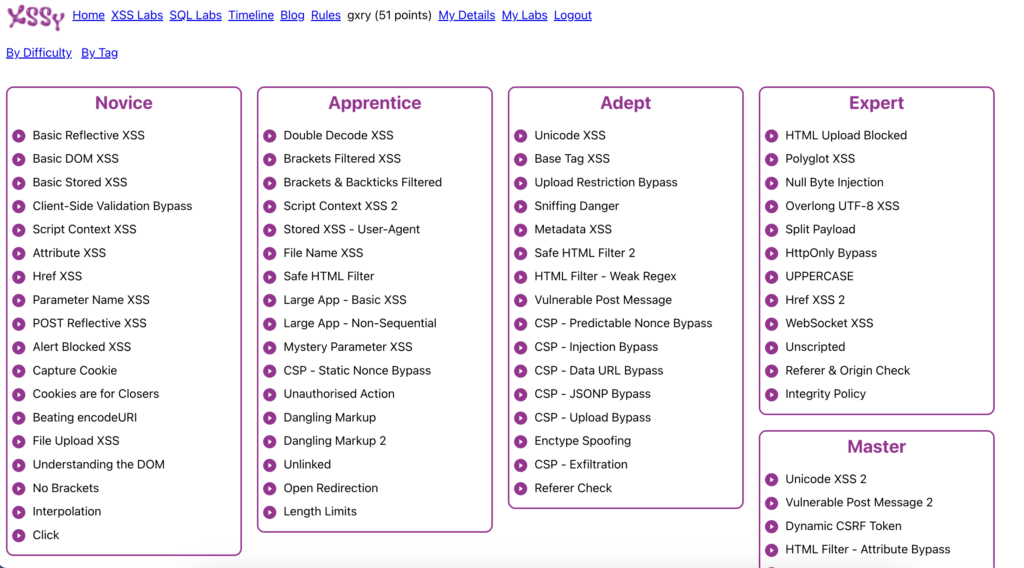
As the name states, Xssy hosts a range of XSS challenges in a CTF format. User’s are given a vulnerable page and a goal, 99% being “leak this flag/cookie and submit your payload”. Payloads are then built within the user’s browser, refined and submitted to the platform to execute in a headless browser to confirm the objective has been complete.
What the platform offers?
- A wide range of XSS challenges, from easy (Novice) through to hard (Master).
- Recently, SQL injection challenges have been added to the platform, expanding the range of challenges.
- Point based ranking system, points scale across difficulties and are achieved upon challenge completion.
- Community driven challenges/content, allowing anyone to submit challenges to the platform.
- Payload hosting lab, to allow “external” payloads to be delivered to the platform.
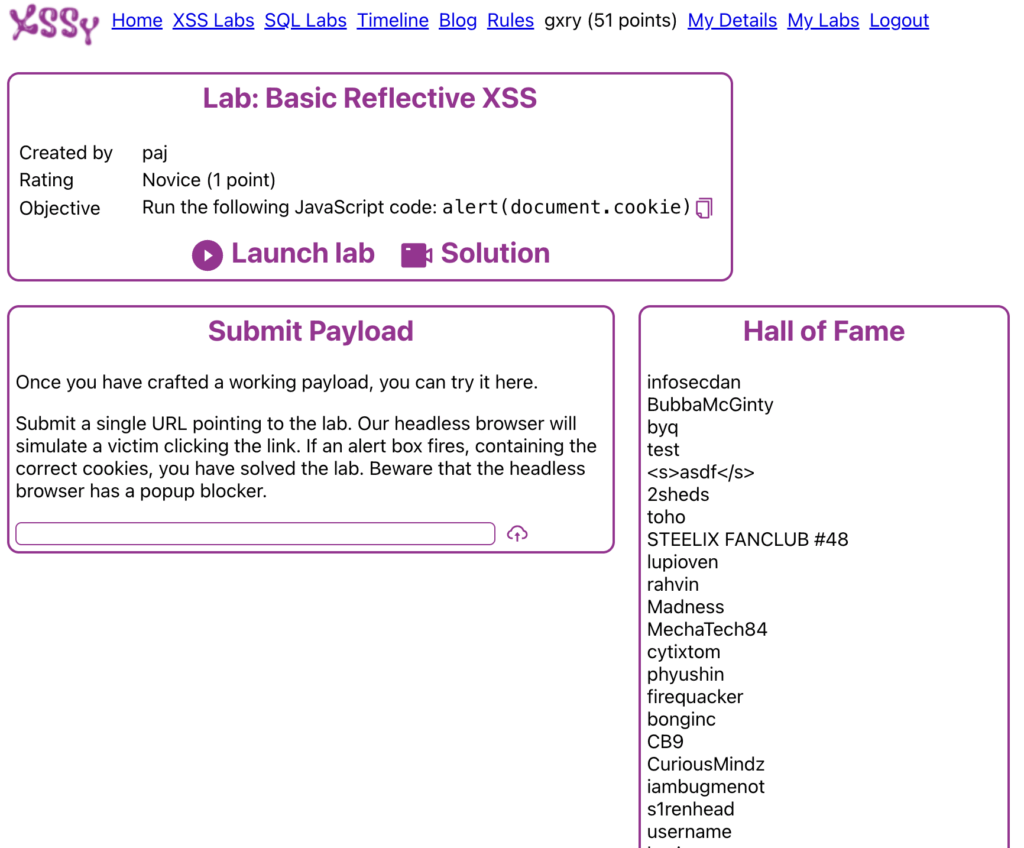
Basic Lab Example
Labs are very simple and straight to the point. Out of the labs I have completed so far (All of Novice, and about 80% of Apprentice) there has been a single objective on a very simple looking web app. Unlike other CTF platforms, the user knows their goal. They are given an input field (or similar) and their goal is to get XSS to pop and leak a flag/cookie. Nothing is hidden behind hours of enumeration. Xssy wants you to craft a working payload, bypassing the challenge obstacles, and move on.
Payload Hosting
A cool feature of Xssy is the ability to host payloads in an “external” manner, allowing your submitted payloads to perform external calls to more complex payloads that can be delivered as a script. This would allow you to submit a payloads such as:
<script src="https://...../x.js">The contents of these files are added and stored in the “My Labs” section of the website. Raw source pages, such as .html and .js, can be created, stored and served to the platform.
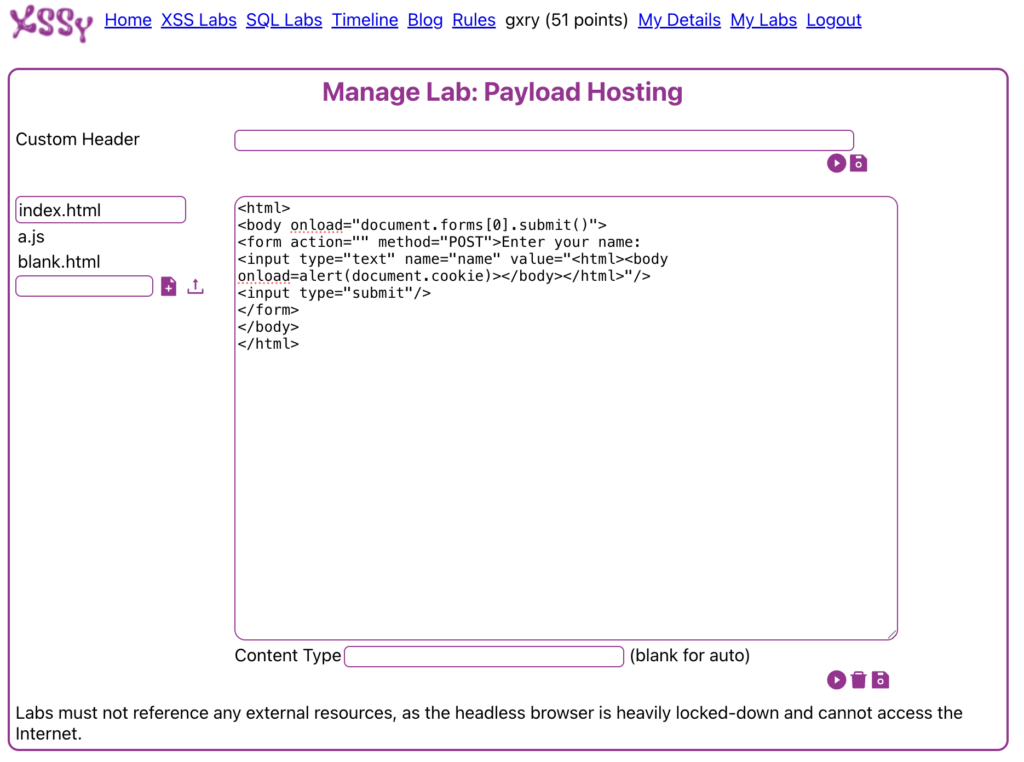
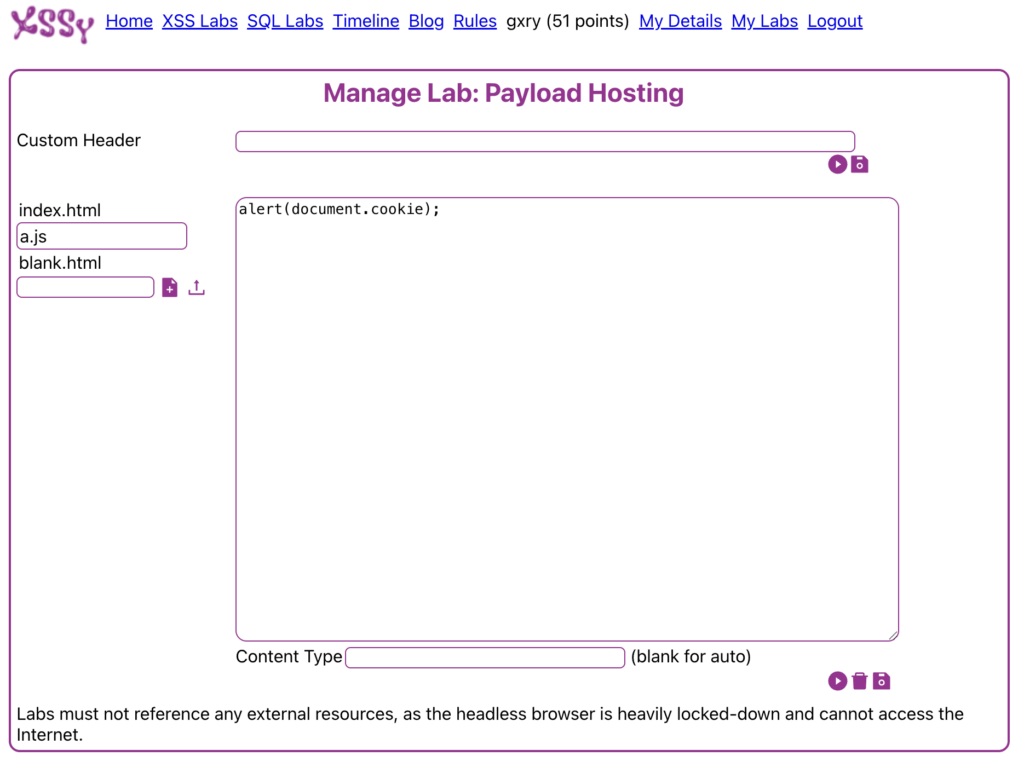
Once tested and saved, the URL of the payload can be copied and used in the lab solutions. There is a short blog post by the developer of Xssy detailing how this works and some firewall/stack implementation to allow this approach in a “safe” manner, see https://xssy.uk/blogItem/the-xssy-tech-stack for detail.
Conclusion
I like this platform. It’s simple, light weight, straight to the point and has a clear focus. No slow loading times, no overly complex UI choices and best of all it’s free.
It’s giving me a fully working playground to focus on specific XSS vulnerabilities and crafting working payloads. If you need somewhere to practice these types of issues without overheads, sign up and get hacking!
Thanks to the creator and challenge builders. I’m having a great time so far 🤘🏻